In the ever-evolving landscape of cyber threats, adversaries continue to innovate, finding new ways to exploit legitimate tools for malicious purposes. One of the latest examples comes from APT41, a well-known Chinese state-sponsored threat group, which has been caught using Google Calendar as a stealthy command-and-control (C2) channel.
This technique, recently detailed by researchers, highlights just how creative and dangerous cyber attackers can be when blending in with normal, everyday digital behavior.
Introducing “Calendarwalk”: Malware Hiding in Plain Sight
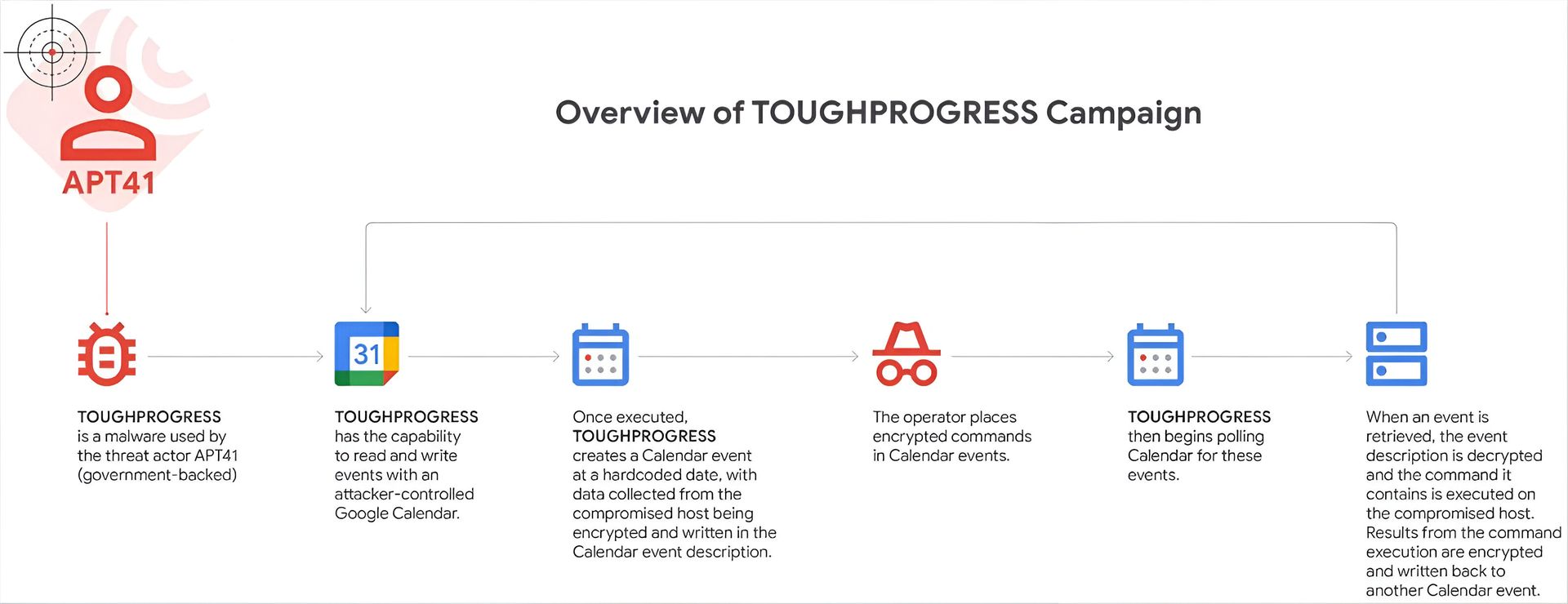
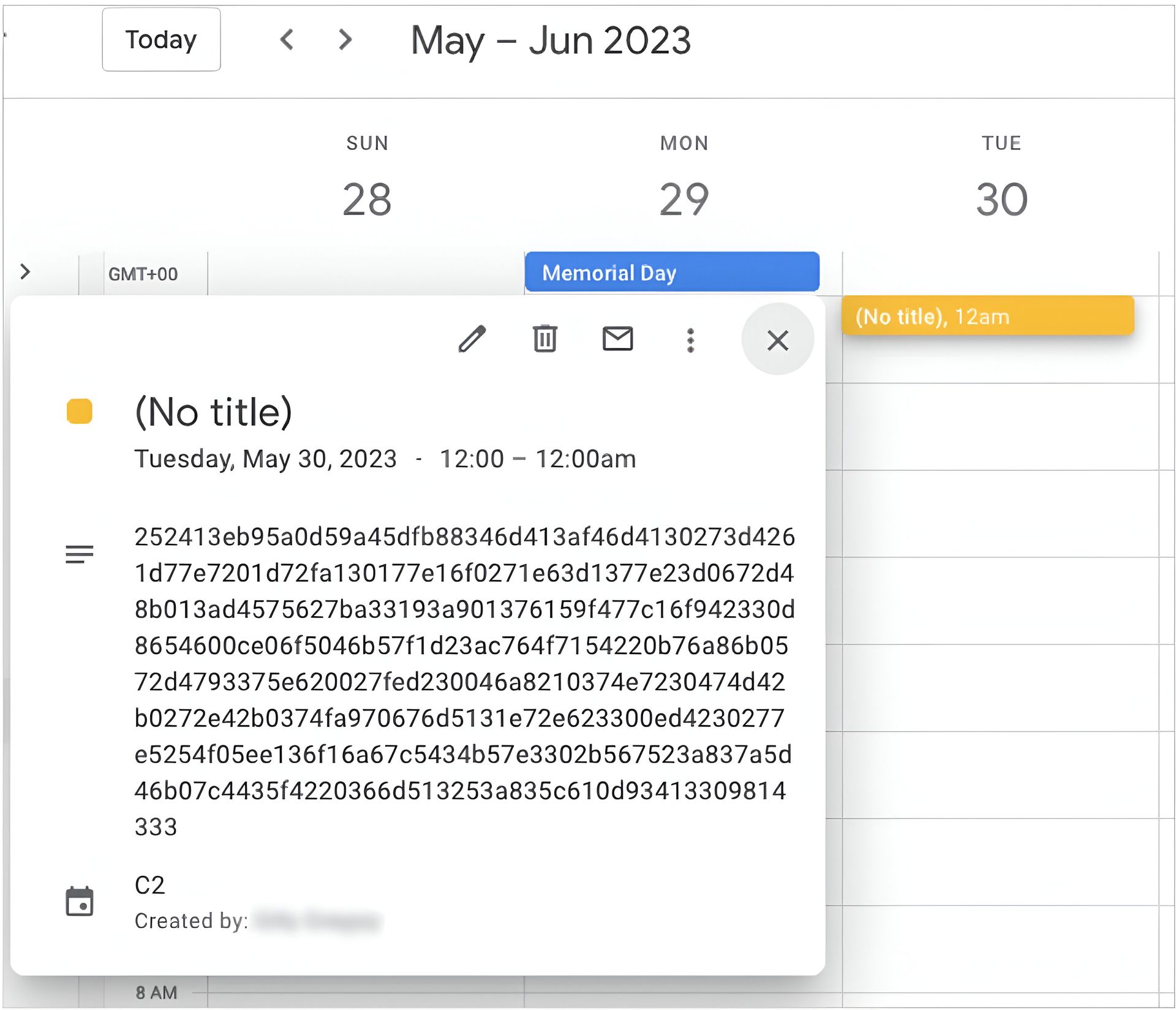
The malware in question, dubbed Calendarwalk, represents a significant step forward in stealthy C2 tactics. Instead of relying on traditional infrastructure that can be blacklisted or blocked, Calendarwalk communicates through Google Calendar events. Commands from the attackers are embedded within calendar entries and retrieved by the infected host—effectively allowing malware to “live off the land” by piggybacking on trusted services.
This method is particularly dangerous because it camouflages malicious behavior under the guise of normal, routine calendar usage, bypassing many traditional detection mechanisms.
Exploiting Red Team Tools: Abuse of GC2
APT41 isn’t stopping at Calendarwalk. The group has also weaponized GC2 (Google Command and Control)—an open-source red teaming tool developed in Go. Originally designed for penetration testing, GC2 has been twisted for malicious use.
Here's how it works:
- Google Sheets is used as a communication channel to issue commands.
- Google Drive is employed to exfiltrate stolen data.
This tactic leverages the trusted status of Google services to evade network defenses and remain undetected within an organization for extended periods.
Why This Matters
The abuse of mainstream cloud services like Google Calendar, Sheets, and Drive marks a significant trend in modern cyber warfare. Known as LOTS (Living Off Trusted Sites), this strategy reduces the need for attackers to set up and maintain traditional C2 infrastructure. Even more concerning, it allows their activity to blend in with legitimate traffic, making it significantly harder to detect and prevent.
How Organizations Can Defend Themselves
These new tactics may be stealthy, but they are not unbeatable. Here’s how organizations can defend against them:
1. Enhance Monitoring and Detection
Use security tools that go beyond simple URL filtering and IP blacklists. Look for solutions that can monitor user behavior and identify anomalies in how services like Google Calendar are being used.
2. Adopt a Zero Trust Architecture
Zero Trust means never assuming trust by default. Enforce strict verification for every user and device accessing your network, especially for cloud-based tools.
3. Educate Your Workforce
Phishing remains a common delivery method for malware. Train employees to be cautious of unsolicited calendar invites and unfamiliar shared documents.
4. Restrict and Audit Cloud Access
Use administrative controls to limit who can create or share calendar events, access Google Drive, or interact with Google Sheets. Regularly audit these permissions.
Final Thoughts
APT41’s abuse of Google Calendar is a stark reminder that cyber attackers are always looking for new ways to fly under the radar. By blending into trusted services, they make detection harder than ever. However, with the right blend of technology, policies, and user awareness, organizations can stay a step ahead.
In the fight against advanced persistent threats like APT41, vigilance and adaptability are key.